The word is getting around about ChatGPT and its variants. You can trust it as much as Google for accurate search results. I have been conducting "interviews" with ChatGPT to measure its chops, and I find its answers stubbornly persistent, consistent, and uniform - it simply will not tell the truth about certain topics and rather lead you down the rabbit hole.
AI
The combination of AI and the world's food supply is in its infancy stage and will advance rapidly if Bill Gates has anything to say about it. He has been obsessing over "cow-burps" and "cow-farts" for years, unable to do anything about them until AI came on the scene.
AI
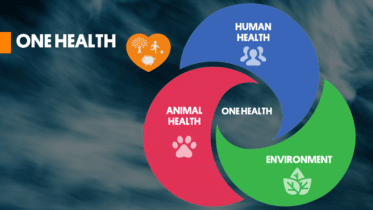
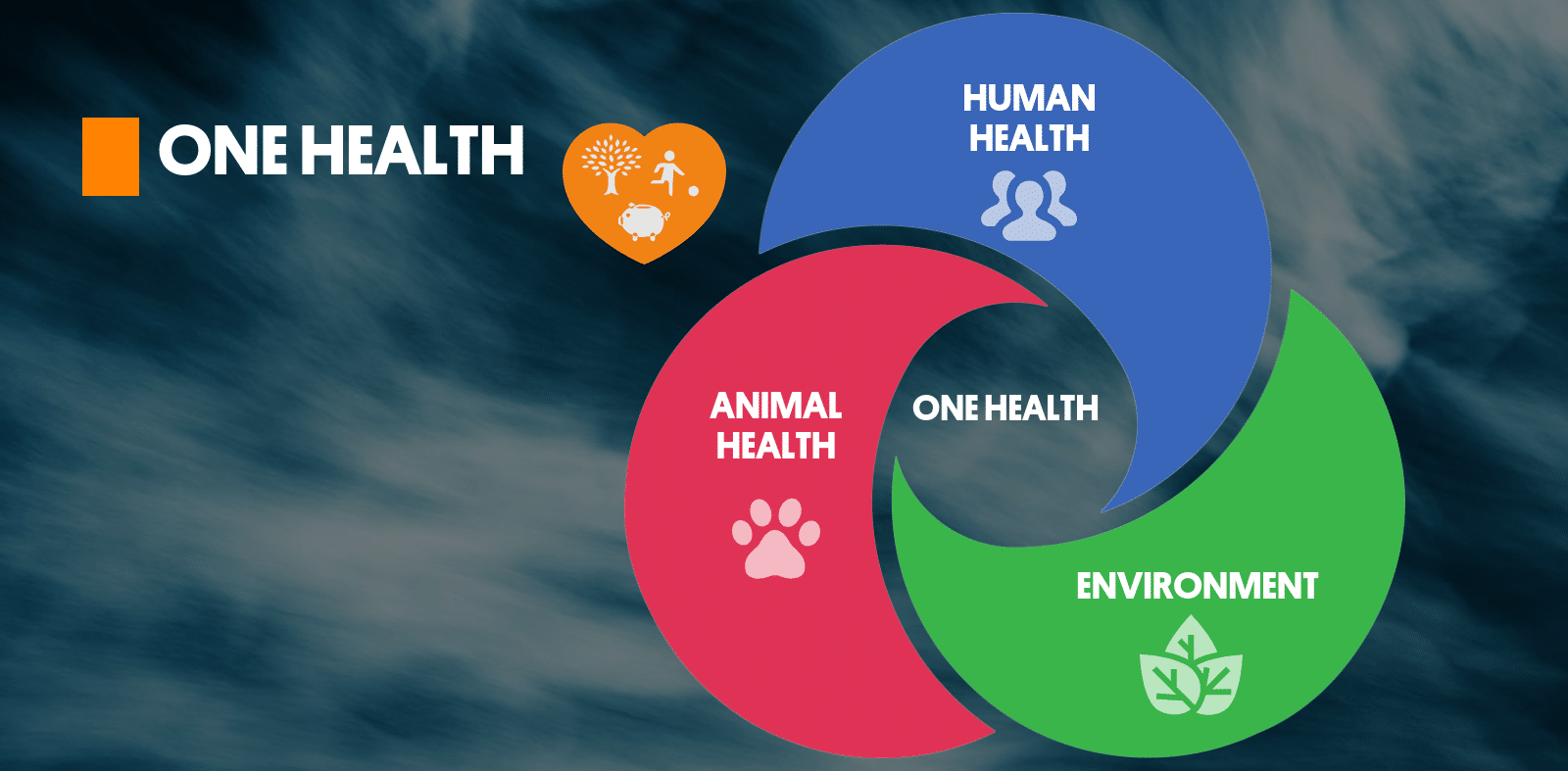
In the heat of the Great Panic of 2020 (COVID-mania), the UN started signing up publishers around the world to support its globalist narrative regarding the Sustainable Development Goals. Wrapped into the SDGs was support for the World Health Organization (WHO) and its strategy for "One Health." In less than 4 years, the publishing world has sung the praises of One Health.
Sustainable Development
2030 Agenda, Sustainable Development
How Did States, Cities Embrace UN’s “2030 Agenda” Climate Action Plans?
WEF Boasts That 98% Of Central Banks Are Adopting CBDCs
72 Types Of Americans That Are Considered “Potential Terrorists” In Official Government Documents
Physician Claims ChatGPT Is Programmed To “Reduce Vaccine Hesitancy”
Russian Journalist Calls Out The EU As A Technocracy
Transhumanism, Digital Twins And Technocratic Takeover Of Bodies
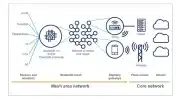
Skynet Has Arrived: Google Follows Apple, Activates Worldwide Bluetooth LE Mesh Network
UBI: Red States Fight Urge To Give ‘Basic Income’ Cash To Residents
Technocracy, Total Surveillance Society
Hall Of Shame II: Thanks To Congress, The NSA Is ‘Just Days From Taking Over The Internet’
Hall Of Shame: Congress Votes For Warrantless Surveillance Of Americans
Technocracy: “The Science Of Social Engineering” And The End Of Debt
Most Recent Daily Podcasts
Climate Change
Islands That Climate Alarmists Said Would Soon “Disappear” Due To Rising Sea Found To Have Grown In Size
The American revolt against green energy has begun
John Podesta: Portrait Of A Consummate Technocrat (And Climate Czar)
Scientists: Your Breath Is Now A Source Of Greenhouse Gas
Jail Time For Operators Of Gas-Powered Leaf Blowers, Edgers, Mowers?
Technocracy
Russian Journalist Calls Out The EU As A Technocracy
Hall Of Shame II: Thanks To Congress, The NSA Is ‘Just Days From Taking Over The Internet’
Bill Gates & UN Behind “Digital Public Infrastructure” For Global Control
Australian Senate Approves Digital ID, America Is Next
The Most Censored Subjects On Earth: The Trilateral Commission, Technocracy & Transhumanism
2030 Agenda
How Did States, Cities Embrace UN’s “2030 Agenda” Climate Action Plans?
15-Minute City: This Statement Should Be Read At Every City Council Meeting In America
King Charles Plots To Accelerate UN 2030 Agenda Goals And Complete Digitization Of Humanity
UN Extends Authority To Manage “Extreme Global Shocks”
Dutch Farmers Rebel: UN’s 2030 Agenda Is Behind Draconian AG Shutdown
Sustainable Development
Flashback: When The UN Launched ‘SDG Publishers Compact’ In October 2020
In the heat of the Great Panic of 2020 (COVID-mania), the UN started signing up publishers around the world to support its globalist narrative regarding the Sustainable Development Goals. Wrapped into the SDGs was support for the World Health Organization (WHO) and its strategy for “One Health.” In less than 4 years, the publishing world has sung the praises of One Health.
Read More